951 | Add to Reading ListSource URL: www.luceor.comLanguage: English - Date: 2014-12-09 10:20:08
|
|---|
952 | Add to Reading ListSource URL: www.cl.cam.ac.ukLanguage: English - Date: 2006-08-24 11:53:33
|
|---|
953 | Add to Reading ListSource URL: oasis.northgrum.comLanguage: English - Date: 2012-10-10 15:15:00
|
|---|
954 | Add to Reading ListSource URL: www.oig.dol.govLanguage: English - Date: 2013-12-17 17:07:37
|
|---|
955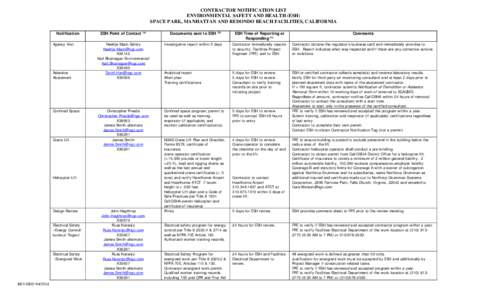 | Add to Reading ListSource URL: oasis.northgrum.comLanguage: English - Date: 2014-09-04 18:05:12
|
|---|
956 | Add to Reading ListSource URL: ereg.naic.orgLanguage: English - Date: 2015-05-01 12:36:29
|
|---|
957 | Add to Reading ListSource URL: www.cl.cam.ac.ukLanguage: English - Date: 2006-08-25 05:54:48
|
|---|
958 | Add to Reading ListSource URL: www.landwehr.orgLanguage: English - Date: 2014-08-18 19:00:02
|
|---|
959 | Add to Reading ListSource URL: www.igtcglobal.comLanguage: English - Date: 2014-03-19 08:56:09
|
|---|
960 | Add to Reading ListSource URL: www.securingthehuman.orgLanguage: English - Date: 2015-05-04 12:26:36
|
|---|